In the ever-evolving landscape of the digital age, the concept of cyber hygiene has never been more critical for businesses. Much like personal hygiene practices are essential for maintaining good health, cyber hygiene practices are vital for safeguarding a company’s digital health against a backdrop of increasingly sophisticated cyber threats. These threats, ranging from malware attacks to phishing schemes, pose significant risks to businesses, potentially leading to severe data breaches, financial losses, and irreparable damage to reputations. Below you will find five essential daily habits that can dramatically improve your organization’s cyber security posture. By integrating these practices into your daily operations, you can create a robust defense mechanism that not only protects your business’s valuable assets but also secures the trust of your clients and business partners.
What is Cyber Hygiene?
Cyber hygiene refers to the practices and steps that users of computers and other devices take to maintain system health and improve online security. These practices are akin to routine measures that help prevent infections and diseases in the realm of personal health. In the context of business, cyber hygiene plays a pivotal role in protecting against an array of cyber threats that are becoming increasingly sophisticated. Poor cyber hygiene can leave businesses vulnerable to a host of adverse outcomes, including data breaches that expose sensitive customer information, financial losses from theft or ransom demands, and lasting damage to a company’s reputation. Such breaches not only erode customer trust but can also attract heavy regulatory fines and legal challenges.
To illustrate its critical importance, here are three recent high-profile cyber-attacks due to poor cyber hygiene measures:
- Anonymous Sudan DDoS Attacks: In a surprising turn of events, a hacktivist group known as Anonymous Sudan launched DDoS attacks against some of the largest tech firms in the world. These attacks took down services and websites, including Microsoft’s Outlook, OneDrive, and the Azure portal. The attacks gained significant media attention due to their impact on such major firms and highlighted the vulnerabilities even large corporations face against coordinated cyber threats.“
- Air Europa Data Breach: Spanish airline Air Europa experienced a significant data breach where hackers accessed financial information of its customers. The breach exposed sensitive data, including card numbers, expiration dates, and CVV numbers, prompting the airline to advise customers to cancel their credit cards. This breach is a stark reminder of the potential financial implications of cyber-attacks on both businesses and their customers.”
- 3CX Supply Chain Attack: The North Korean Lazarus hacking group breached 3CX, a company known for its Voice Over Internet Protocol (VOIP) software used worldwide. This supply chain attack allowed the attackers to push malicious software updates to users, stealing data and credentials. This incident underscores the sophisticated nature of cyber threats and the importance of securing the software supply chain.”
Why Adhere to Good Cyber Hygiene?
Adhering to robust cyber hygiene practices offers a multitude of benefits. It safeguards critical data against unauthorized access and ensures the integrity and availability of information, which is crucial for business operations and customer confidence. Effective cyber hygiene also fosters a culture of security awareness within the organization, ensuring that employees become the first line of defense against cyber threats. Moreover, compliance with industry regulations and data protection standards not only mitigates the risk of legal complications but also positions the business as a trustworthy and reliable entity in the eyes of customers and partners. In essence, good cyber hygiene is not just about preventing cyber attacks; it’s about creating a secure, resilient, and trusted environment that supports the business’s growth and sustainability.
5 Daily Habits to Protect Your Business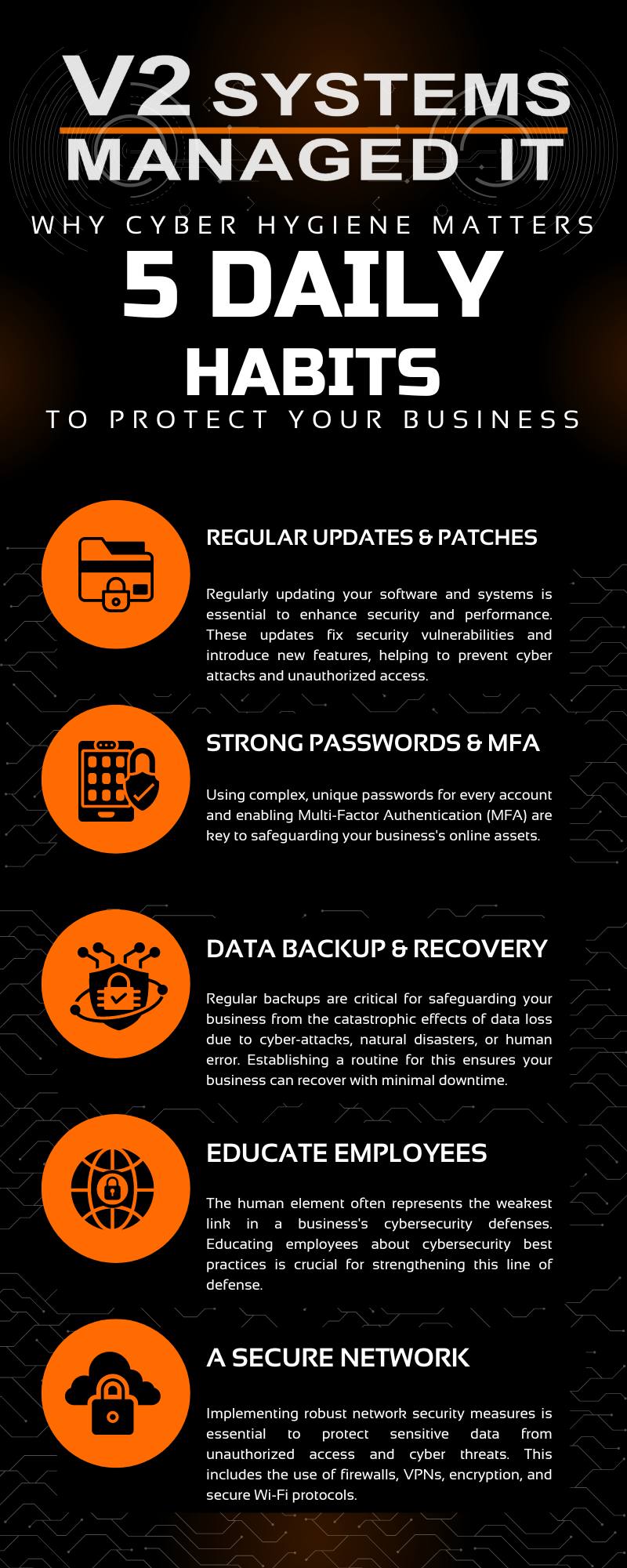
Implementing Cyber Hygiene Practices
Integrating effective cyber hygiene practices into daily operations is a step-by-step process that can significantly enhance your business’s security posture. Start by conducting an audit of your current cybersecurity measures to identify areas of improvement. Educate your team on the importance of these practices through regular training sessions, focusing on the critical habits discussed, such as password security, system updates, and data backup strategies. Establish clear policies and procedures for employees to follow, ensuring they understand their roles in maintaining cyber hygiene. For a more tailored approach to safeguarding your digital assets, consider consulting with cybersecurity experts or managed service providers like V2 Systems. These professionals can offer personalized advice and implement solutions that are specifically designed to meet your business’s unique needs and challenges. By taking proactive steps and leveraging expert guidance, you can build a robust defense against cyber threats, protecting your business and its valuable data.
Contact us today to learn how we can help secure your digital environment and ensure your peace of mind in the ever-evolving world of cyber threats.
By Kelly Weist
Since 1995, V2 Systems has employed local systems administrators, network engineers, security consultants, help desk technicians and partnering companies to meet a wide range of clients’ IT needs, from research, to implementation, to maintenance. Concentrate on your VISION…We’ll handle the TECHNOLOGY!

